200-201 CBROPS
200-201 Threat Hunting and Defending using Cisco Technologies for CyberOps
Cisco
CyberOps Associate
200-201, 200-201 dumps, 200-201 exam questions, 200-201 pdf, Cisco CBROPS 200-201 certification exam, latest 200-201 dumps, latest 200-201 exam questions, lead4pass 200-201 dumps, new 200-201 dumps
admin
0 Comments
[Update Dec 2022] latest 200-201 dumps to help you pass the Cisco CBROPS certification exam

Using the Latest update leads4pass 200-201 dumps can help you successfully pass the Cisco CBROPS certification exam on your first attempt.
Because 200-201 dumps have many success advantages:
- Lightweight Learning Tool (PDF+VCE)
- More free usage time (365 days Free Update)
- Covers all Cisco CBROPS practical exam questions and answers, with explanations of difficult problems
- Have a professional Cisco technical team service
So why not use 200-201 dumps to help you easily and successfully pass the exam? And leads4pass, as the provider of 200-201 dumps, has many years of industry reputation, is the industry leader, and is trustworthy, what else do you have to worry about?
Therefore, it is strongly recommended that you use the 200-201 dumps https://www.leads4pass.com/200-201.html (PDF+VCE), which is up to date throughout the year, to prepare you for a career leap.
More detailed Latest 200-201 CBROPS certification information:
Vendor: Cisco
Exam Code: 200-201
Exam Name: Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS)
Certification: CyberOps Associate
Duration: 120 minutes
Languages: English
Price: $300 USD
Number of Questions: 95-105
200-201 dumps: https://www.leads4pass.com/200-201.html (Update Dec 2022, 264 Q&A)
Sharing some of the latest 200-201 dumps pdfs for candidate testing
https://drive.google.com/file/d/1NvgnmVOH2wzbAtjRlNnpN57M70GgdSeW/view?usp=share_link
https://drive.google.com/file/d/1Hq9tXhs7kyJzL3cTTXNNYoTOKZOld2X7/view?usp=share_link
https://drive.google.com/file/d/1jiweTttTSynQKmfr1o7J_vTVYc49oIUI/view?usp=share_link
Read some of the latest 200-201 Dumps exam questions and answers online
| Number of exam questions and answers | Exam name | From | Release time | Last updated |
| 15 | Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) | leads4pass | Dec 02, 2022 | 200-201 dumps |
New Question 1:
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
A. The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
B. The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
C. The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
D. The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
Correct Answer: D
New Question 2:
How does TOR alter data content during transit?
A. It spoofs the destination and source information protecting both sides.
B. It encrypts content and destination information over multiple layers.
C. It redirects destination traffic through multiple sources avoiding traceability.
D. It traverses source traffic through multiple destinations before reaching the receiver
Correct Answer: B
New Question 3:
Which two elements are used for profiling a network? (Choose two.)
A. session duration
B. total throughput
C. running processes
D. listening ports
E. OS fingerprint
Correct Answer: AB
A network profile should include some important elements, such as the following:
Total throughput is the amount of data passing from a given source to a given destination in a given period of time Session duration is the time between the establishment of a data flow and its termination Ports used a list of TCP or UDP processes that are available to accept data Critical asset address space the IP addresses or the logical location of essential systems or data Profiling data are data that system has gathered, these data help for incident response and to detect incident Network profiling = throughput, sessions duration, the port used, Critical Asset Address Space Host profiling = Listening ports, logged in accounts, running processes, running tasks, applications
New Question 4:
Refer to the exhibit.

Which field contains DNS header information if the payload is a query or a response?
A. Z
B. ID
C. TC
D. QR
Correct Answer: B
New Question 5:
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
A. forgery attack
B. plaintext-only attack
C. ciphertext-only attack
D. meet-in-the-middle attack
Correct Answer: C
New Question 6:
Refer to the exhibit.
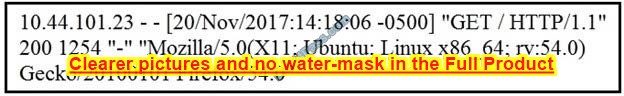
What does the message indicate?
A. an access attempt was made from the Mosaic web browser
B. a successful access attempt was made to retrieve the password file
C. a successful access attempt was made to retrieve the root of the website
D. a denied access attempt was made to retrieve the password file
Correct Answer: C
New Question 7:
Which regular expression matches “color” and “colour”?
A. colo?ur
B. col[08]+our
C. colou?r
D. col[09]+our
Correct Answer: C
New Question 8:
What are the two characteristics of the full packet captures? (Choose two.)
A. Identifying network loops and collision domains.
B. Troubleshooting the cause of security and performance issues.
C. Reassembling fragmented traffic from raw data.
D. Detecting common hardware faults and identifying faulty assets.
E. Providing a historical record of a network transaction.
Correct Answer: CE
New Question 9:
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
A. NetScout
B. tcpdump
C. SolarWinds
D. netsh
Correct Answer: B
New Question 10:
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A. file extension associations
B. hardware, software, and security settings for the system
C. currently logged-in users, including folders and control panel settings
D. all users on the system, including visual settings
Correct Answer: B
New Question 11:
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A. The computer has HIPS installed on it.
B. The computer has a NIPS installed on it.
C. The computer has a HIDS installed on it.
D. The computer has a NIDS installed on it.
Correct Answer: C
New Question 12:
Refer to the exhibit.

Which component is identifiable in this exhibit?
A. Trusted Root Certificate stored on the local machine
B. Windows PowerShell verb
C. Windows Registry hive
D. local service in the Windows Services Manager
Correct Answer: C
https://docs.microsoft.com/en-us/windows/win32/sysinfo/registry-hives https://ldapwiki.com/wiki/HKEY_LOCAL_MACHINE#:~:text=HKEY_LOCAL_MACHINE%20Windows%20registry%20hive%20contains,detected%20hardware%20and%20device%20d rivers.
New Question 13:
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which technology makes this behavior possible?
A. encapsulation
B. TOR
C. tunneling
D. NAT
Correct Answer: D
Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.
New Question 14:
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on the network traffic?
A. true negative
B. false negative
C. false positive
D. true positive
Correct Answer: B
A false negative occurs when the security system (usually a WAF) fails to identify a threat. It produces a “negative” outcome (meaning that no threat has been observed), even though a threat exists.
New Question 15:
An engineer needs to configure network systems to detect command and control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology should be used to accomplish the task?
A. digital certificates
B. static IP addresses
C. signatures
D. cipher suite
Correct Answer: A
…
The CyberOps Associate certification exam covers knowledge and skills related to security concepts, security monitoring, host-based analysis, network intrusion analysis, and security policies and procedures. The Core exam (200-201 CBROPS) is unique.
Select leads4pass 200-201 dumps https://www.leads4pass.com/200-201.html, Helping you 100% pass the Cisco 200-201 CBROPS certification exam.
