CompTIA
CompTIA Security+ Exam certification
comptia security+ sy0-501
comptia security+ sy0-501 dumps
comptia security+ sy0-501 dumps pdf
comptia security+ sy0-501 pdf
comptia security+ sy0-501 practice questions
comptia security+ sy0-501 practice test
comptia security+ sy0-501 study guide
comptia security+ sy0-501 study guide pdf free download
sy0-501 dumps, sy0-501 exam dumps pdf, sy0-501 practice questions, sy0-501 study guide
admin
0 Comments
[2020.3] Successfully pass the CompTIA SY0-501 exam for free to obtain SY0-501 exam dumps
How to succeed through CompTIA Security+ SY0-501 exam? Share the latest SY0-501 exam dumps, SY0-501 pdf, and online hands-on tests for free to improve skills and experience, with leads4pass providing the latest and complete CompTIA Security+ SY0-501 dumps: https://www.leads4pass.com/sy0-501.html (Latest Update)
Free effective CompTIA Security+ SY0-501 video tutorial
CompTIA Security+ SY0-501 exam pdf free download
[PDF Q1-Q13] Free CompTIA Security+ SY0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1I6AeFlwFg7mH6Zh8o0A3yrnDmf46CxHT
Security+ (Plus) Certification | CompTIA IT Certifications: https://www.comptia.org/certifications/security
The CompTIA Security+ exam will certify the successful candidate has the knowledge and skills required to install and configure
systems to secure applications, networks, and devices; perform threat analysis and respond with appropriate mitigation techniques; participate in risk mitigation activities; and operate with an awareness of applicable policies, laws, and regulations. The successful candidate will perform these tasks to support the principles of confidentiality, integrity, and availability.
Latest Updated CompTIA Security+ SY0-501 Online Exam Practice Questions
QUESTION 1
Which of the following precautions MINIMIZES the risk from network attacks directed at multifunction printers, as well as
the impact on functionality at the same time?
A. Isolating the systems using VLANs
B. Installing a software-based IPS on all devices
C. Enabling full disk encryption
D. Implementing a unique user PIN access functions
Correct Answer: A
QUESTION 2
A company determines that it is prohibitively expensive to become compliant with new credit card regulations. Instead,
the company decides to purchase insurance to cover the cost of any potential loss. Which of the following is the
company doing?
A. Transferring the risk
B. Accepting the risk
C. Avoiding the risk
D. Migrating the risk
Correct Answer: A
QUESTION 3
An information security specialist is reviewing the following output from a Linux server.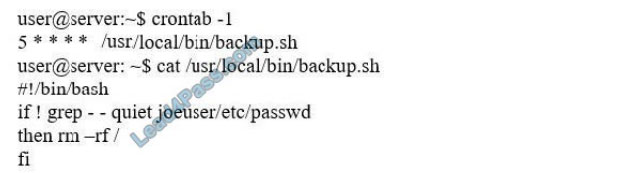
Based on the above information, which of the following types of malware was installed on the server?
A. Logic bomb
B. Trojan
C. Backdoor
D. Ransomware
E. Rootkit
Correct Answer: A
QUESTION 4
To reduce disk consumption, an organization\\’s legal department has recently approved a new policy setting the data
retention period for sent email at six months. Which of the following is the BEST way to ensure this goal is met?
A. Create a daily encrypted backup of the relevant emails.
B. Configure the email server to delete the relevant emails.
C. Migrate the relevant emails into an “Archived” folder.
D. Implement automatic disk compression on email servers.
Correct Answer: A
QUESTION 5
An employee uses RDP to connect back to the office network.
If RDP is misconfigured, which of the following security exposures would this lead to?
A. A virus on the administrator\\’s desktop would be able to sniff the administrator\\’s username and password.
B. Result in an attacker being able to phish the employee\\’s username and password.
C. A social engineering attack could occur, resulting in the employee\\’s password being extracted.
D. A man in the middle attack could occur, resulting the employee\\’s username and password being captured.
Correct Answer: D
QUESTION 6
A security analyst is implementing PKI-based functionality to a web application that has the following requirements: File
contains certificate information Certificate chains Root authority certificates Private key
All of these components will be part of one file and cryptographically protected with a password. Given this scenario,
which of the following certificate types should the analyst implement to BEST meet these requirements?
A. .pfx certificate
B. .cer certificate
C. .der certificate
D. .crt certificate
Correct Answer: A
QUESTION 7
A company wants to ensure that the validity of publicly trusted certificates used by its web server can be determined
even during an extended internet outage. Which of the following should be implemented?
A. Recovery agent
B. Ocsp
C. Crl
D. Key escrow
Correct Answer: B
QUESTION 8
A company wants to implement a wireless network with the following requirements:
All wireless users will have a unique credential.
User certificates will not be required for authentication.
The company\\’s AAA infrastructure must be utilized.
Local hosts should not store authentication tokens.
Which of the following should be used in the design to meet the requirements?
A. EAP-TLS
B. WPS
C. PSK
D. PEAP
Correct Answer: D
QUESTION 9
A security analyst is performing a quantitative risk analysis. The risk analysis should show the potential monetary loss
each time a threat or event occurs. Given this requirement, which of the following concepts would assist the analyst in
determining this value? (Select two.)
A. ALE
B. AV
C. ARO
D. EF
E. ROI
Correct Answer: AC
QUESTION 10
Which of the following is the appropriate network structure used to protect servers and services that must be provided to
external clients without completely eliminating access for internal users?
A. NAC
B. VLAN
C. DMZ
D. Subnet
Correct Answer: C
QUESTION 11
A company is terminating an employee for misbehavior. Which of the following steps is MOST important in the process
of disengagement from this employee?
A. Obtain a list of passwords used by the employee.
B. Generate a report on outstanding projects the employee handled.
C. Have the employee surrender company identification.
D. Have the employee sign an NDA before departing.
Correct Answer: C
QUESTION 12
A manager suspects that an IT employee with elevated database access may be knowingly modifying financial
transactions for the benefit of a competitor. Which of the following practices should the manager implement to validate
the concern?
A. Separation of duties
B. Mandatory vacations
C. Background checks
D. Security awareness training
Correct Answer: A
QUESTION 13
A corporation is concerned that, if a mobile device is lost, any sensitive information on the device could be accessed by
third parties. Which of the following would BEST prevent this from happening?
A. Initiate remote wiping on lost mobile devices
B. Use FDE and require PINs on all mobile devices
C. Use geolocation to track lost devices
D. Require biometric logins on all mobile devices
Correct Answer: A
Share leads4pass discount codes for free 2020

About the benefits and introductions of leads4pass
leads4pass offers the latest exam exercise questions for free! CompTIA exam questions are updated throughout the year. leads4pass has many professional exam experts! Guaranteed valid passing of the exam! The highest pass rate, the highest cost-effective! Help you pass the exam easily on your first attempt.

Summarize:
Allexamalert shares the latest CompTIA Security+ SY0-501 exam dumps, SY0-501 pdf, SY0-501 exam exercise questions for free. You can improve your skills and exam experience online to get complete exam questions and answers guaranteed to pass the exam we recommend leads4pass SY0-501 exam dumps
Latest update leads4pass Security+ SY0-501 exam dumps: https://www.leads4pass.com/sy0-501.html (730 Q&As)
[Q1-Q13 PDF] Free CompTIA Security+ SY0-501 pdf dumps download from Google Drive: https://drive.google.com/open?id=1I6AeFlwFg7mH6Zh8o0A3yrnDmf46CxHT
